The First Step to a Zero Trust Solution
Start With Rock-Solid Identity and Access Management
Stepping Ahead with Identity and Privileged Access Management
Heightened threats call for a zero trust model. Achieve it with a singular platform—the Bravura Security Fabric. It is the only integrated identity and privileged access platform that enforces automated policies across authentication, identity, governance, and privilege access management so the right people access the right resources at the right time regardless of their location, device or network.
Zero trust model
Leverage the investments you already have with a security model that integrates natively with the other platforms you are using, including SIEM or other centralized management and alerting to make life easier so you don’t have to manually correlate alerts and reduce false positives.
Inventory Identities
Get a near instant inventory of the ever expanding identity ecosystem vying for trust that needs to be brought into governance. Auto-detection lists new, added, or changed moved identities.
Adapt cybersecurity
Weave progressive and adaptive access models and policies with the speed and depth only one platform can provide across your workforce and tech stack. It offers the greatest visibility, security assurance, and support for hybrid IT including multicloud infrastructure.
Largest ecosystem of connectors
Bravura Security has the largest organically grown ecosystem of connectors and its Bravura Discover gives you the visibility to further your threat intelligence around your entire ecosystem.
Manage lifecycles
Maintain a tight control surface to protect your environment with automation, including APIs for full customization. Ensure your organization robustly controls and manages identity and privileged access throughout the full lifecycle.
Eliminate always-on access
Provide audited and brokered Just In Time (JIT) access that activates just enough privileges to perform only the desired task and promptly revokes privileges and reduces the attack surface once the activity is complete.
Auto-detect changes
Automatically detect and probe over 10,000 systems per hour for new and changed identities or newly elevated privilege changes made out of band to manage and minimize your attack surface.
Govern exceptions
In a 'trust but verify first' culture, dynamic security formulas that mitigate risk include exceptions but automated policies minimize exceptions so only the true outliers need additional management.
Appropriately authenticate
Use four types of zero trust authentication through local applications, cloud or on-premises directories, or federated to best suit applications and protect against credential-focused cyber attacks:
- Synchronize and periodically change credentials to enhance security
- Make logins more convenient and enforce a strong password policy with federated single sign-on (SSO)
- Enable Security Assertion Markup Language (SAML) for the most secure federated authentication
- Add multi-factor authentication (MFA) for another protection against the internal and external threats
Mitigate risk
Further reduce exposure to your systems and data with the threat detection and response solution — Bravura Discover which presents a birds-eye view of your organization’s current attack surface so you can protect it.
Live and On-Demand Webinars

Top Cybersecurity Outcomes a Zero Trust Model Delivers
Organizations turning to zero trust security models to protect their resources and data are realizing substantial business benefits and outcomes.
WATCH NOW
The Zero Trust Journey with Identity and Privileged Access Management
Zero trust and legacy workflows can coexist as you tackle one business process at a time as your organization enhances operational maturity and cybersecurity resilience.
WATCH NOW
Planning Your Zero Trust Journey With Enhanced Identity Governance
Embarking on a journey to build a zero trust security model for your organization may feel daunting. But there are actionable steps you can take to get started.
Watch Now
Protecting Your Privileged Access in a Zero Trust Security Model
Gain practical insight into how to implement controls that establish and maintain contextual, adaptive trust to protect privileged access.
Watch nowStart the Conversation
Worksheet
Embarking on a journey to build a zero-trust security model for your organization may feel daunting. Take the first step in planning your zero trust journey by using this worksheet to start a conversation with your stakeholders.
Download Now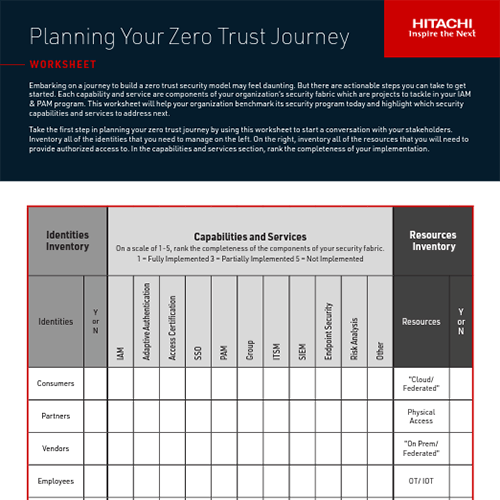
Zero Trust is A Journey, Not a Destination
Ebook
Start an actionable game plan for your next security model with this starter guide on adaptable access management and dynamic Zero Trust developed in partnership with the global enterprise security company intiGrow.
Download Now
Get a Zero Trust Pre-Assessment
Roadmap for Your Organization
Not sure where to start? You're not alone. Get a roadmap for your zero trust security model from our partner, intiGrow. A global enterprise security company, intiGrow delivers comprehensive security solutions and competitively priced security services to empower you to achieve business-enabling defense-in-depth security postures, manage risk, improve compliance, and proactively detect and prevent threats. intiGrow, a trusted information security leader, provides robust and diverse security solutions and services to hundreds of financial services, insurance, health care, retail, and telecom companies.
Start your assessment
Bravura Security Blog
What Is the Difference Between PAM, PIM and PUM?
When it comes to managing restricted access within an organization’s IT and digital assets, systems administrators have many factors to consider when granting privileges. IT decision-makers need to prioritize cybersecurity while also providing a way ...
Read MoreReducing Risk in the Joiner-Mover-Leaver Identity Process Landscape
Hiring new employees and awarding promotions from within can be promising for company growth — but challenging for IT teams. The job market is hot, filled with millions of openings and new hires. For the HR and IT departments, it leads to the ...
Read MoreReduce Risk Through a Just-in-Time Approach with Bravura Privilege
Credentials are the keys you use to access everything from your email account to your organization’s most sensitive data. These keys are not all created equal. Sure, you always need to have access to your email. Does the same hold true for ...
Read MoreInterested in learning more about Zero Trust?
Bravura Security professionals and partners would welcome the opportunity to collaborate on your zero trust strategy to accelerate your cybersecurity posture.
Contact Us Now